Imagine you’re trying to verify one transaction out of 500 in a Bitcoin block. Downloading the whole block would take minutes on a slow connection. But what if you only needed to check nine pieces of data instead? That’s the power of Merkle trees - a simple, brilliant structure that makes blockchain verification fast, lightweight, and secure.
What Exactly Is a Merkle Tree?
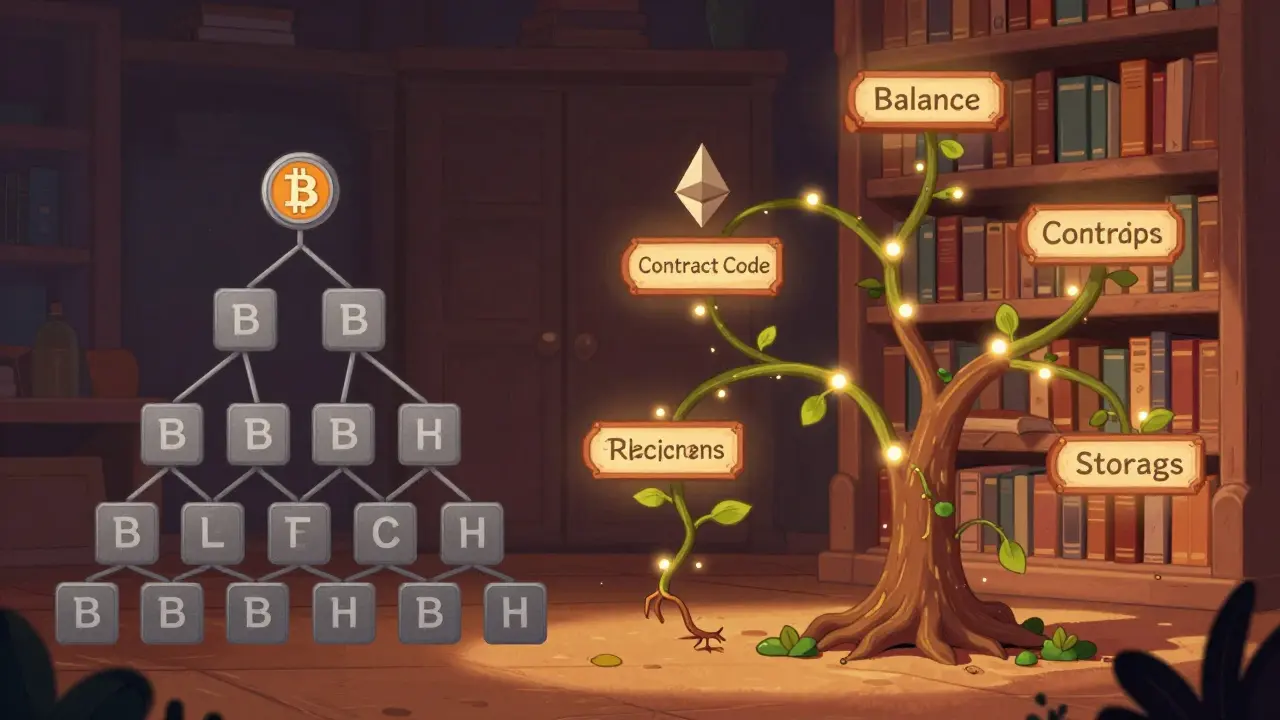
A Merkle tree is a binary tree made of hashes. Each leaf node holds the hash of a single piece of data - like a transaction. Every parent node holds the hash of its two children. You keep combining pairs of hashes upward until you reach one final hash at the top: the Merkle root.
This isn’t just math. It’s a security feature. If even one transaction changes, its hash changes. That changes its parent’s hash. Then its grandparent’s. And so on - until the Merkle root becomes completely different. So if someone tries to tamper with a transaction, the root hash won’t match the one stored in the block header. The network instantly knows something’s wrong.
Ralph Merkle invented this in 1988. Back then, it was meant to improve digital signatures. Today, it’s the silent engine behind Bitcoin and Ethereum’s ability to prove data integrity without downloading everything.
How Bitcoin Uses Merkle Trees
Bitcoin’s job is simple: move value securely. It doesn’t need to run apps or store complex state. So its Merkle tree is lean and focused - just transactions.
Each Bitcoin block header contains six fields. One of them is the Merkle root. That root is the hash of every transaction in that block, compressed into a single 32-byte value. When a lightweight wallet (called an SPV client) wants to check if your payment made it into the blockchain, it doesn’t download the whole block. It only downloads the block header - about 80 bytes - and asks a full node for a Merkle proof.
A Merkle proof is a short list of sibling hashes. Let’s say you’re verifying transaction #247. The node gives you the hashes of the other transactions it needs to combine with yours, step by step, up to the root. You take your transaction hash, combine it with the first sibling, hash the result, combine that with the next sibling, and so on. If the final hash matches the Merkle root in the block header, your transaction is confirmed. No need to trust the node. You verified it yourself with just nine hashes, even if the block had 500 transactions.
This is why mobile wallets like BlueWallet or Blockchain.com work on your phone. They’re not storing 500 GB of blockchain data. They’re trusting the math, not the server.
Ethereum’s Advanced Version: The Merkle Patricia Trie
Ethereum does more than send money. It runs smart contracts, stores account balances, tracks token ownership, logs events, and more. So it needs more than a simple transaction tree. Enter the Merkle Patricia Trie.
This isn’t just a binary tree. It’s a hybrid: part Merkle tree, part Patricia trie (a type of prefix tree). It can store key-value pairs efficiently and supports updates without rebuilding the whole structure. Ethereum uses four of them in every block:
- State Trie: Stores all account data - balances, nonce, contract code, storage root.
- Transaction Trie: Lists all transactions in the block in order.
- Receipt Trie: Holds logs and gas used for each transaction after execution.
- Storage Trie: Each contract has its own, storing variables like token balances or NFT ownership.
When you call a smart contract, Ethereum doesn’t just check if the transaction was included. It checks if your account had enough balance, if the contract code was valid, and if the result matches what the network agreed on. All of this is verified using Merkle proofs - but now across multiple trees.
For example, if you want to prove you own 100 DAI, you don’t need the whole blockchain. You get a proof from the state trie showing your account’s balance, signed by the Merkle root. The same system lets you prove you received an airdrop, without the project having to store every recipient’s address on-chain.

Why the Difference Matters
Bitcoin’s Merkle tree is like a receipt scanner. You scan the barcode (the root) and verify one item (your transaction). Simple. Fast. Secure.
Ethereum’s Merkle Patricia Trie is like a living library. Every book (account) has its own catalog (storage trie), and every checkout (transaction) gets logged with a timestamp (receipt). You can check out any book, update its notes, and the whole system stays consistent.
Bitcoin’s design prioritizes security and simplicity. Ethereum’s prioritizes flexibility and programmability. That’s why Bitcoin blocks average 500 transactions - easy to verify. Ethereum blocks can have thousands of transactions and hundreds of contract calls - and still verify them all with proofs.
The trade-off? Ethereum needs more storage and CPU power. A full Ethereum node stores state data that’s over 1 TB and growing. Bitcoin’s full node stores transaction history - also huge, but simpler to validate.
Real-World Uses Beyond Crypto
Merkle trees aren’t just for blockchains. Git uses them to track code changes. If you revert to an old commit, Git doesn’t re-download the whole project. It checks hashes of file changes using a Merkle-like structure.
BitTorrent and IPFS use them to verify file chunks. When you download a movie from multiple peers, each piece is hashed. Your client checks the Merkle root to make sure no chunk was corrupted or replaced with malware.
Database systems like MongoDB and Cassandra use Merkle trees to sync data between nodes. Instead of transferring entire tables, they exchange root hashes. If they don’t match, only the differing parts are synced.
This isn’t niche tech. It’s foundational infrastructure. It’s why your phone can hold a crypto wallet. It’s why you can verify your NFT ownership without running a node. It’s why decentralized systems can scale without central servers.
What’s Next? Verkle Trees and Beyond
Merkle trees are old but not perfect. Proof sizes can still be large - especially in Ethereum, where you need to prove state across multiple tries. That’s why Ethereum developers are testing Verkle trees.
Verkle trees use a different kind of math - polynomial commitments instead of hash functions. This lets them create much smaller proofs. Instead of 20 hashes to prove a transaction, you might need just 2 or 3. That means faster sync times, lighter nodes, and better mobile performance.
Ethereum’s upcoming upgrades are already planning to switch. Bitcoin might follow if SPV becomes too slow. But for now, Merkle trees remain the gold standard - proven, reliable, and running the backbone of the $2+ trillion crypto market.
Why You Should Care
You don’t need to understand cryptography to use Bitcoin or Ethereum. But knowing how Merkle trees work helps you trust them.
When your wallet says "confirmed," it’s not just trusting a server. It’s running a mathematical check - using hashes, sibling nodes, and a root - to prove you weren’t lied to. That’s why decentralized systems can exist without banks, governments, or middlemen.
Every time you send crypto from your phone, you’re using a 37-year-old idea that lets you verify truth without asking anyone for permission. That’s not magic. That’s Merkle trees.
What is the Merkle root in Bitcoin?
The Merkle root is the top hash of all transactions in a Bitcoin block. It’s stored in the block header and allows lightweight wallets to verify transactions without downloading the entire block. If any transaction changes, the Merkle root changes, making tampering obvious.
How does SPV verification work?
SPV (Simple Payment Verification) lets a lightweight wallet confirm a transaction by requesting a Merkle proof from a full node. The wallet combines its transaction hash with provided sibling hashes, recalculates up the tree, and checks if the result matches the Merkle root in the block header. No full blockchain download needed.
Why does Ethereum use a Merkle Patricia Trie instead of a simple Merkle tree?
Ethereum needs to track account balances, contract storage, and transaction receipts - not just transactions. The Merkle Patricia Trie is a more complex structure that can efficiently store and update key-value pairs. It supports dynamic state changes, which a basic binary Merkle tree can’t do without rebuilding the whole tree.
Can Merkle trees be hacked?
Not if the underlying hash function is secure. Merkle trees rely on cryptographic hash functions like SHA-256 (Bitcoin) and Keccak-256 (Ethereum). These are designed to be collision-resistant - meaning it’s computationally impossible to find two different inputs that produce the same hash. So tampering with data changes the root hash, which is easily detectable.
Do I need to understand Merkle trees to use crypto?
No. Wallets and apps handle all the verification behind the scenes. But understanding them helps you know why your crypto is secure without trusting a company or server. It’s the difference between believing someone told you your money is safe - and knowing the math proves it.

Jon Martín
Merkle trees are the unsung heroes of crypto man
One hash at the top and boom you know everything's legit without downloading the whole damn blockchain
It's like having a fingerprint for a library and being able to check if one book was swapped without opening every shelf
Simple genius
Danyelle Ostrye
This is why I don't trust centralized exchanges
They don't use Merkle proofs they just say 'your balance is fine'
Meanwhile my phone wallet checks the math myself
That's real freedom right there
Jordan Leon
The elegance of Merkle trees lies in their recursive structure. Each hash is a deterministic function of its children, creating an immutable chain of verification. This property, rooted in information theory and cryptographic hashing, enables trust minimization at scale. It is not merely a data structure-it is a protocol for decentralized epistemology. The fact that this was conceived in 1988, before smartphones or even widespread internet adoption, speaks to the profundity of its design. We are still building upon it today.
greg greg
Let me break this down even further because people keep missing the bigger picture. A Merkle tree isn't just about saving bandwidth-it's about enabling trustless verification across an adversarial network where no participant can be assumed honest. Every single hash in the proof acts as a cryptographic checkpoint, and the entire structure is designed so that even if 99% of the nodes are malicious, the one honest node providing the sibling hashes can't lie without breaking the math. And the beauty is, you don't need to know who that node is-you just need to know the hash function is secure. That's why Bitcoin can run on a Raspberry Pi and still be as secure as a full node. The math doesn't care about your hardware, only about the integrity of the inputs. And that's why Ethereum's move to Verkle trees is such a big deal-they're replacing hash functions with polynomial commitments, which compress proof sizes exponentially, meaning future light clients won't just be fast, they'll be nearly zero-cost to run on a smartwatch. This isn't an upgrade-it's a paradigm shift in how we think about distributed consensus.
Denise Paiva
So Merkle trees are the reason your phone wallet works cool I guess
But let’s be real-Ethereum’s whole system is just overengineered chaos
Four tries just to track who owns what
It’s like building a Ferrari with a toaster inside
Bitcoin’s one tree and it’s still standing after 15 years
Ethereum needs a new database every six months
Just saying
Calen Adams
SPV is the MVP of crypto adoption hands down
Merkle proofs let you verify without syncing 500GB
That’s why we have millions of non-custodial wallets on phones
Meanwhile traditional finance still makes you wait 3 days for a wire
And they call us crazy
Also Verkle trees are the future-polynomial commitments are next level
Once Ethereum flips the switch it’s gonna be insane how fast sync times drop
Light clients will be lighter than your Spotify cache
Valencia Adell
Everyone acts like Merkle trees are this brilliant innovation
But they’re just hash chains with extra steps
And Ethereum’s Patricia Trie? A glorified hashmap with a fancy name
It’s slower, more complex, and harder to audit
Meanwhile Bitcoin’s simplicity is why it’s still alive
Ethereum’s codebase is a dumpster fire of patches
And you call this progress?
It’s just complexity for complexity’s sake
Sarbjit Nahl
It is imperative to note that the Merkle tree paradigm is not inherently superior to centralized verification mechanisms. It merely shifts trust from institutional entities to cryptographic assumptions. The security of the system is contingent upon the unbroken integrity of hash functions, which are themselves subject to theoretical vulnerabilities under quantum computing. Furthermore, the assumption that lightweight clients are more secure is fallacious, as they rely on full nodes for data, thereby introducing new attack vectors. The narrative of decentralization through Merkle trees is thus a rhetorical construct rather than an absolute truth.
Paul Johnson
why do people overcomplicate this
its just hashes man
hash the tx hash hash the next one keep going
top hash = proof
if you change one tx the whole thing breaks
its not magic its math
and ethereum with their 4 tries is just being extra
like why not make a whole new database for your socks while your at it
bitcoin just works
Meenakshi Singh
Verkle trees are the real MVP 🚀
Imagine proving your balance with 2 hashes instead of 20
That’s not an upgrade-it’s a revolution
And yes I’m still salty Ethereum didn’t launch with this from day one 😤
But hey at least they’re fixing it before it’s too late
Bitcoin better start paying attention or get left behind 🤷♀️
Kelley Ramsey
This is so cool!!! I never realized how elegant this is!!!
It’s like the blockchain is whispering to your phone, ‘Hey, your transaction is here, and I can prove it without telling you everything!’
And the fact that this was invented in 1988??
Like, who even thought of this??
It’s beautiful how math can create trust without people…
It’s almost spiritual…
Thank you for explaining this so clearly!!!
I’m going to share this with my cousin who thinks crypto is just a scam!!!
Michael Richardson
Bitcoin’s Merkle tree? Clean.
Ethereum’s? Overkill.
US tech bros love complexity because they think it equals intelligence.
Meanwhile, the rest of the world uses Bitcoin to send money.
Case closed.
Krista Hoefle
merkle trees? more like merkle pretzles
all that hashing just to prove one tx
why not just use a database
or better yet
ask the server
youre not saving that much bandwidth anyway
and ethereum? lol
they need a whole library to track a balance
its like using a jet engine to power a bicycle